
Smartphone hacking is unfortunately a real phenomenon that makes your data and privacy vulnerable. Even hacking phone cameras is possible, which allows hackers to access your phone’s camera even if you are not using it.
Just like how you take precautions to protect your mobile phone using smartphone accessories like protective cases and screen protectors, it is important to invest in protecting your smartphone data as well.
In this post, we look at tell-tale signs of your mobile phone being hacked and how you can prevent falling prey to hackers’ tricks and traps.
What is Phone Hacking?
Hacking phones is the process by which an intruder accesses and exploits your mobile phone or its communications, either remotely or by physical theft.
How are Phones Hacked?
Knowing the different ways that the hacking of phones takes place will help you with understanding the issue and how to protect your smartphone from hacking.
Smartphone Hacking Software

Smartphone hacking software might end up on your phone as a smartphone hacking app deceptively disguised as a regular mobile app, through browsing unreliable websites on your phone’s browser, or via a phishing attack. Hacking software then can cause issues through the following methods:
Keylogging
The hacker gets to snoop on what you type, tap, or say on your phone.
Trojan
These malware extract data from your phone while remaining disguised to avoid detection.
Smartphone Phishing Attacks
Phishing attacks on your smartphone can be similar to the ones you encounter on your computer. These attacks are performed via emails, texts, instant messaging, and other communication forms. They are usually made to look legitimate and might ask you to share private codes, click on links, or other such tricks. When you fall for these attacks, you may end up inadvertently handing over your private data yourself, or via malware that they ask you to install.
Smartphone Bluetooth Hacking
Keeping your Bluetooth on constantly not only drains your phone’s battery but also exposes it to the possibility of being hacked. Bluetooth hacking relies on sophisticated technology that allows the hacker to access your mobile phone as long as the devices are within a range of 30 feet/10 metres.
Smartphone SIM Card Swapping
Social hacking is now easier than ever. Since many people share a lot of their personal information online, hackers can use this information to impersonate them. In a SIM card swapping scam, a hacker can impersonate you and request a new SIM from your service provider. Once the hacker has the SIM, your SIM gets deactivated and the hacker now controls your phone calls and messages.
Physical Theft
This is a straightforward approach. The hacker steals your phone and cracks into it via brute force password guessing or by applying hacking software. In this scenario, once in your smartphone, the hacker has access to all the data and potentially all the sites and apps you are signed into.
How to Know if Your Phone is Hacked?

Now that you have become aware of smartphone hacking tools and approaches, here are some symptoms of a hacked phone.
Your Battery Drains Faster
There are many reasons why your battery may be draining quickly. With our guide to battery life, you can eliminate some of the possible causes of battery drain. However, if the issue is not with your phone or its battery, then it could potentially be caused by malware and fraudulent apps.
Your Phone’s Performance is Abnormally Low
Unless your phone has a very old chipset and is overloaded with demanding apps, low performance could hint at something malicious. Hackers’ software or applications on your phone might cause it to unexpectedly freeze, crash or restart.
Unfamiliar Calls or Texts on Your Smartphone
Phone spying software, SMS trojans and other hacking smartphone tools could be the reason behind those outgoing calls and messages. It could also be that someone is impersonating you to steal your data via social hacking.
Strange Activity on Your Online Accounts
Prompts for password resets, unusual login activity, or verification notifications from your social media accounts, emails, and other such accounts could be a strong indication of hacking. If you have not requested changes, or your activity log looks unusual, it could be a hacker who has gained access to your phone.
How to Protect Your Phone from Hacking
Before you end up searching “how to know if someone is spying on your phone”, here are a few ways how you can save your phone from hacking.
Don’t Jailbreak Your Smartphone
Many people choose to jailbreak their phones to have more control over the operating system. Jailbreaking or rooting your device lets you bypass the security barriers that prevent certain user actions such as downloading certain apps.
A rooted phone might prevent security updates from installing on your phone and exposes your device to security threats.
Regularly Install OS and App Updates
New updates for your OS and apps not only fix bugs and tweak the software for better performance, but also deal with any potential loopholes. Make sure you always install security updates to enhance the protection of your data. You can also set automatic updates which will save you time and keep your system up-to-date.
Only Download Reliable Apps
No matter how enticing an app may seem, it is best to only download apps that you are confident in. Apple’s app store vets all the apps available on it to ensure you do not end up with a bad app with potential security risks.
Android users need to be especially vigilant when downloading from the app store, as Google does not have stringent practices in place. It is also recommended that you read their terms of use to ensure that you are not signing away your privacy when using the apps.
Use Hard-to-Crack Passwords
Passwords are the first line of defence in phone hacking protection when your phone is stolen. Use passwords that use a combination of numbers, letters, and symbols with a length of at least 8 characters. Also, avoid using personal information like birthdays, names etc. as these may be easy to guess.
Enable Two-Factor Authentication
Turn on two-factor authentication (2FA) on your device as well as on your apps and social sites. This creates another layer of authentication steps that can deter hackers. Using biometrics like fingerprints and face ID can also help. Having a physical USB key is also helpful in improving the security of your device.
Regularly Clear Your Browser Data
In case of theft, your browser data can provide the hacker with access to bits of your personal life, which they can use for other purposes. It is also advisable to not save your credit card details or passwords in your browser and turn off the autofill feature.
Avoid Storing Passwords on Your Smartphone
With so many apps and sites requiring unique passwords to sign in, you may be tempted to store them all on your device. If you do want to do that, it is best to use secure password manager apps with a reliable reputation.
Use a Lost Device Tracking Service
Apple iPhones come with a native application to find your Apple devices. These applications help find your lost devices before they can be hacked into. You can also find trusted third-party apps that do the same, if your phone does not come with a tracking feature.
Alternatively, you can also use a Bluetooth tracker device like an Apple AirTag Bluetooth Tracker to track lost devices.
Use VPN in Public Spaces
If you need to use a public Wi-Fi service, make sure you are using a Virtual Private Network to do so. Public Wi-Fi does not come with the security that you expect with your home network, and hence these make your smartphones easy targets for hacking.
Do Not Use Public Charging Stations
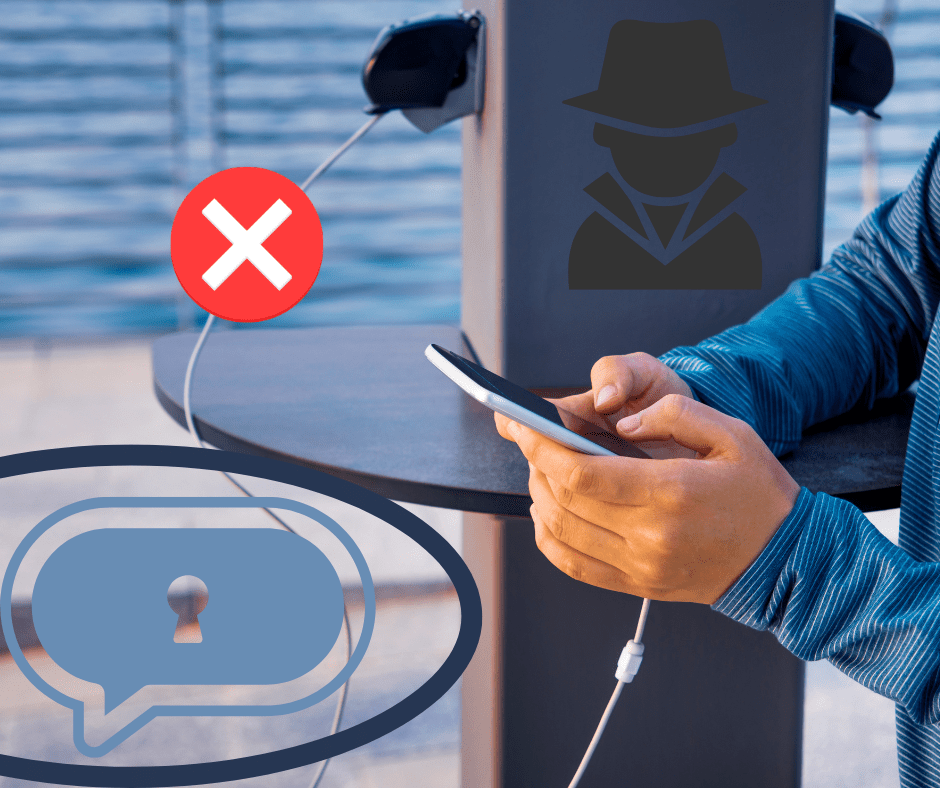
Many public spaces like cafes and airports offer public charging stations with charging cables. Despite the good intention, plugging your mobile phone into a charging cable in public comes with the potential risk of a security breach.
Since charging cables also act as data cables, hackers can disguise their hacking tools as charging points. It is better that you use your phone charger in public. If your phone supports wireless charging, then using a public wireless charging station should not be a problem.
Learn more about wireless charging with our blogpost “Answers to All Your Wireless Charger and Charging Questions”.
Turn Off Lock Screen Messages
Many people set their notifications to display details. This feature, though helpful, might attract potential hackers or give away information that could help hackers. Set all your notifications to not show details when your phone is locked.
We also recommend turning off virtual assistants on the lock screen as a precautionary measure.
Keep Your Private Life Private
Social media has allowed us to share a lot about our lives with the whole world. However, social hacking becomes easier when we share too many details of our lives online. Sharing your live locations can allow hackers to know where to find your phone.
Practise safe and cautious use of social sites and apps to prevent yourself from becoming a hacker’s easy target.
Use Phone Security Apps
Many reputable antivirus and malware protection software companies offer security apps for smartphones. These apps can help improve upon your phone’s existing security and also scan for potential malware and viruses on your device.
Do Not Open Suspicious Links
Avoid clicking on links in SMS texts and emails from contacts that you do not recognise. Also, report these suspicious contacts. Many of these links will encourage you to share your private information or download suspicious apps that will allow hackers to access your smartphone.
Turn Off Bluetooth, GPS, and Other Wireless Features
Bluetooth, Wi-Fi, and in some rare cases NFC hacking are all possible. Turn off these services when not in use and whenever possible set up a security passcode for connections.
Keep Your Device Always with You
You might be in the habit of leaving your smartphone unattended at work or a party. But your best bet to keep your device safe is to always keep it with you to prevent theft.
Set Your Phone to Auto-Lock
Instead of manually locking your phone, set a timer for when your phone can automatically lock after a set period of inactivity. This will help prevent anyone from accessing your phone if you have left it unattended.
Backup Your Smartphone
Backing up your smartphone data will not stop your phone from being hacked. However, in case your phone is hacked, stolen, or lost, you will still have all your important data with you. There are many storage devices that you can use to backup all your data, learn more about them with our post, “Portable Storage Devices: Understanding Portable Digital Data Storage”.
Follow Smartphone Hacking News
Keep yourself updated with the latest in smartphone security and news about new scams and hacking. This will help you avoid falling into a hacking trap and update you on new security features available for your devices.
What to Do If My Phone is Hacked?

There might not be a sure-fire way to deal with a hacked phone on your own. But here are some steps we recommend you take if you believe your mobile phone has been hacked.
Delete Any Suspicious Apps
If you notice a suspicious app on your phone that you do not remember downloading, then it is best to completely uninstall it from your smartphone. Head over to the App Manager on your smartphone and delete the app along with all of its data.
Factory Reset Your Phone
If you feel someone is spying on your phone or has hacked into it, a factory reset might help completely remove them. However, factory resetting your smartphone will erase all the data you have on it, along with all your saved settings and preferences.
To factory reset your iPhone:
- Connect your iPhone to the charger
- Open the Settings app and tap on General
- At the end of the menu, you will find the Reset option
- Once you tap on Reset, select Erase All Content and Settings
- You will be given the option of iCloud Backup. However, we do not recommend it.
- Tap on Erase Now to reset your iPhone
To factory reset your Android phone:
- Connect your smartphone to the charger
- Open the Settings menu, select System, and then the Reset option
- Tap Erase all data
- Enter your PIN when prompted
- Erase all data once again to confirm
Protect Your Accounts
If your device is hacked, you may want to inform services, such as your emailing service, Google account or Apple ID, social media, online banking, or online shopping services. Sites that save your credit card information or banking details can help you report fraudulent transactions to your bank.
Keep The Hackers Out

The risk of having your smartphone hacked can be mitigated by following our suggestions and advice. The safety of your information and privacy is in your hands. Keep yourself updated with the latest news and double-check apps and contacts before engaging with them.
Want to learn more ways to improve your smartphone experience? Looking for accessories for your mobile phone? Get in touch with us!
